What we do
We provide an ever evolving feed with Contextualized Mobile Security intelligence. That data in generated by our own engines and supervised/evolved by security analysts.
How we do it
We deliver the intel via our FEED (B2B, for custom integrations) or WEB. Our feed can be integrate in any intelligence engine (ex: SIEM), portal or be included in any format (reports, dashboards, presentations, etc).
Our Business Model
Our services are subscription based. We mix our own tech and professional supervision in order to achieve best quality levels.
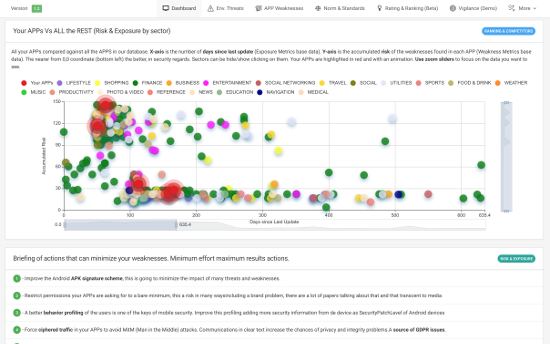
Compare your APPs with competitors.
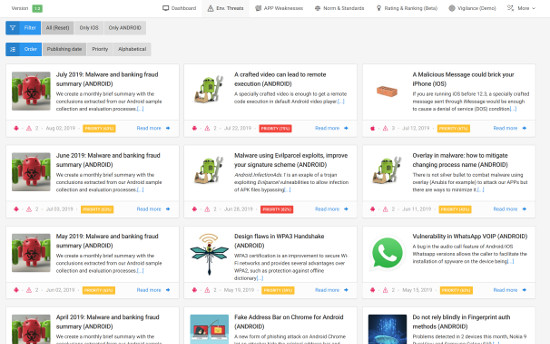
Be aware of Environmental Threats.
Why/when we think you need us
What we can offer to your security ecosystem?
Context is important
We offer contextualized intel, we believe knowing the context is important to make good decisions. Using a multi-source system able us to view more angles in risk management, that helps us to provide context-aware intel.
Quality is our goal
We use use state-of-the-art tech and human expertise to increase the quality level of our intel. We are not focused on selling software or tech. We can compete in cost and quality versus the alternatives.
Adaptability
We want our intel can be integrated in any scenario so we provide a feed with high case-adaptability. SIEMs, intel engines, portals, reports, etc. Chalenge us with a integration case!
Security Audit
If you need to audit your mobile APPs to safisfy any internal or external requirement. If you provide security audit services and you want integrate mobile APP security in your portfolio in a efficient way.
Threat Management
If you need starting intel to forge an integral MTM plan, you would need to know your current status to focus the plan, that is our goal, provide information to help security decisions.
Security Rating of APPs
If you have a Mobile Device Management process and need to evaluate the security of third-party APPs.
Mobile Markets Vigilance
Monitoring official and alternative markets looking for APPs threating your brand. Examples: Malware luring its victims using your brand or outdated versions of your APPs.
Secured Lifecycles
We can attach our process to any step in your development or decision lifecycles.
- Production Env.?
- Pre/Development Env.?
- SIEM?
- Ticket System
- Security Audit Dept.?
- SOC or Security Office?
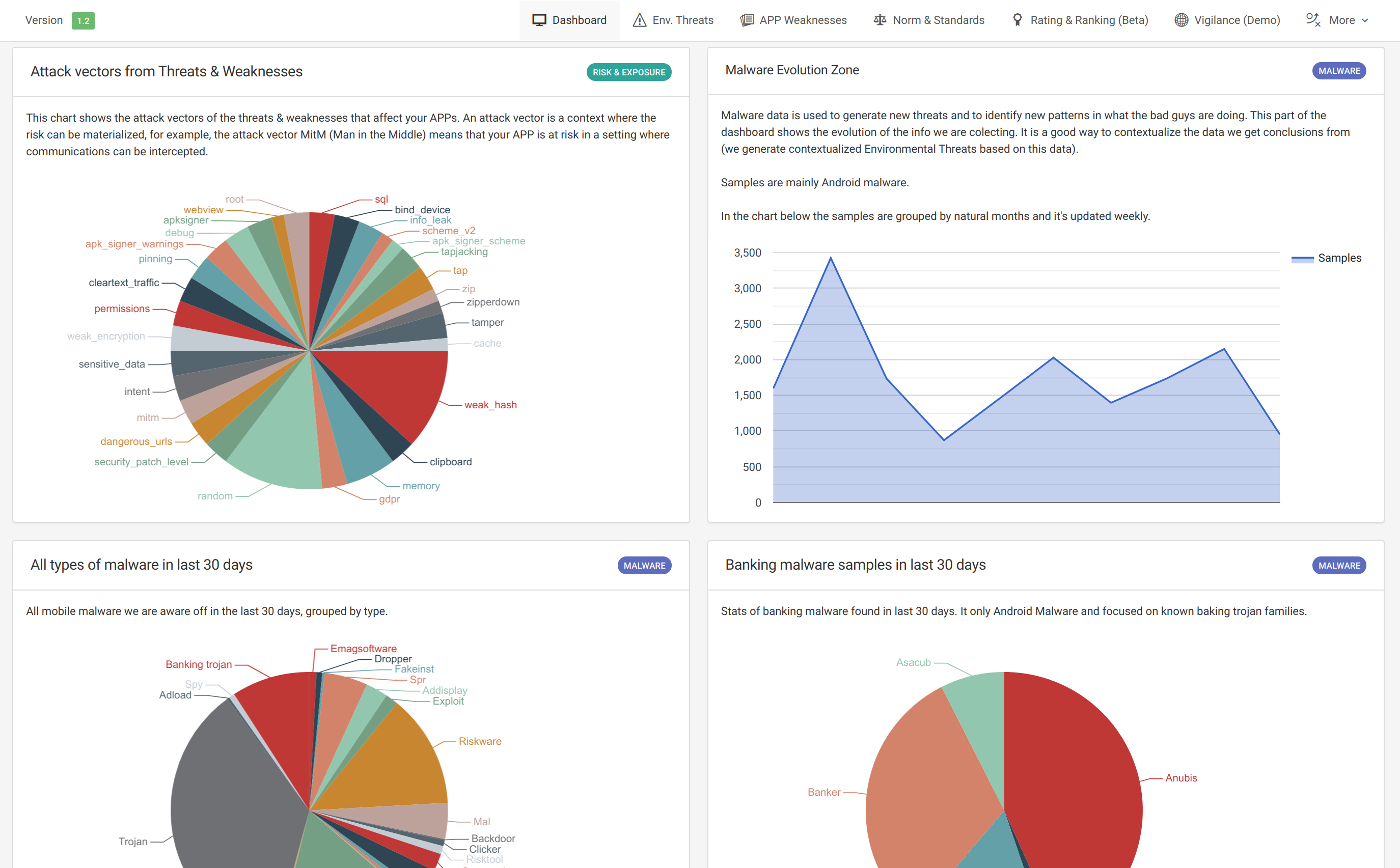
Attack Vectors and Malware.
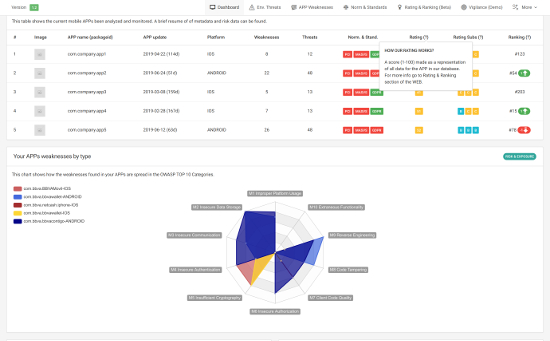
Your analyzed APPs, Rating, Ranking and Owasp Top 10 distribution.
Customers helped so far:




Are you interested?
Contact us to ask for more information, give us feedback or say hello.

